Safeguards Described in the Hipaa Security Rule
Office of Safeguards Mission Statement The Mission of Safeguards is to promote taxpayer confidence in the integrity of the tax system by ensuring the confidentiality of IRS information provided to federal state and local agencies. Covers protected health information PHI in any medium while the HIPAA Security Rule covers electronic protected health information e-PHI.

Breaking Down The Hipaa Security Rule Accountable
Background Subtitle A of Title V of the Gramm-Leach-Bliley Act G-L-B Act or the Act captioned Disclosure of Nonpublic Personal Information Title V limits the instances in which a financial institution may disclose nonpublic personal information about a consumer to nonaffiliated third parties and requires a financial institution to disclose to all of its customers.
. Many of which are described below and the covered entitys legal duties. If an implementation specification is described as required the specification must be implemented. - GitHub - prowler-cloudprowler.
The Security Rule refers to Security Standards for the Protection of Electronic Protected Health Information What technical safeguards are needed. DHHS IT Policies and Standards also serve as guidance to support any division-level security policies. HIPAA Rules have detailed requirements regarding both privacy and security.
Frequently Asked Questions for Professionals - Please see the HIPAA FAQs for additional guidance on health information privacy topics. Prowler is an Open Source security tool to perform AWS security best practices assessments audits incident response continuous monitoring hardening and forensics readiness. Personal data should be protected by reasonable security safeguards against such risks as loss or unauthorized access destruction use modification or disclosure of data.
These safeguards are described in the HIPAA Security Rule as either required or addressable. Keep in mind that HIPAA was written to not only protect PHI but to assist treatment providers in caring for the patient without requiring patient authorization in order to share their PHI. In fact all the safeguards are generally required irrespective of how.
Patient access to their information. Revisions to the HIPAA Security Rule dictate the conditions safeguards that must be in place for HIPAA-compliant storage and the communication of ePHI. For example it is permissible to share protected health information with health care providers who will treat the patient in their office or after.
The concept of addressable implementation specifications was developed to provide covered entities additional flexibility with respect. The HIPAA Security Rule outlines the requirements for the protection of electronic patient health information. The Final Omnibus Rule of 2013.
25 percent of respondents described themselves as fully compliant with the Security Rule and 50 percent described themselves as 85 to 95 percent compliant compared to. Act HIPAA to name a few. Sharing with Health Care Providers.
It contains more than 200 controls covering CIS PCI-DSS ISO27001 GDPR HIPAA FFIEC SOC2 AWS FTR ENS and custom security frameworks. This policy and associated standards provide guidance and define the minimum administrative technical and physical safeguards and procedures necessary to. Safeguards verifies compliance with Internal Revenue Code IRC.

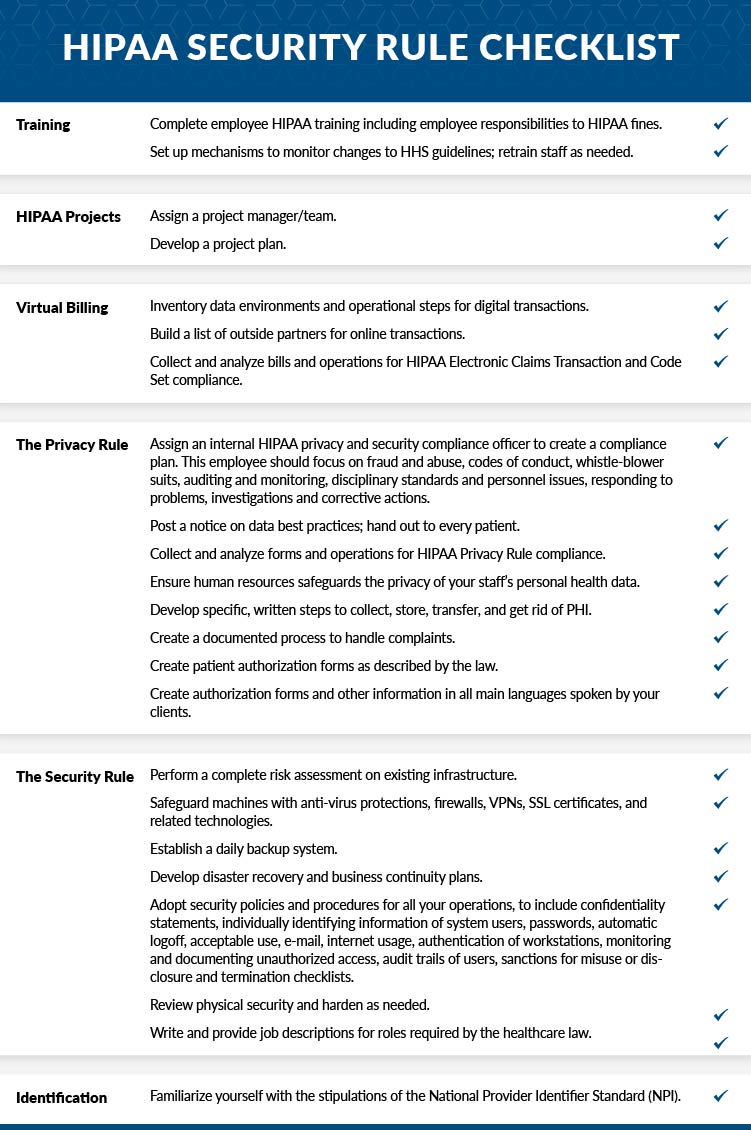
2022 Hipaa Security Rule Checklist What Is The Hipaa Security Rule

What S Administrative Safeguard What Re Hipaa Standards Itperfection
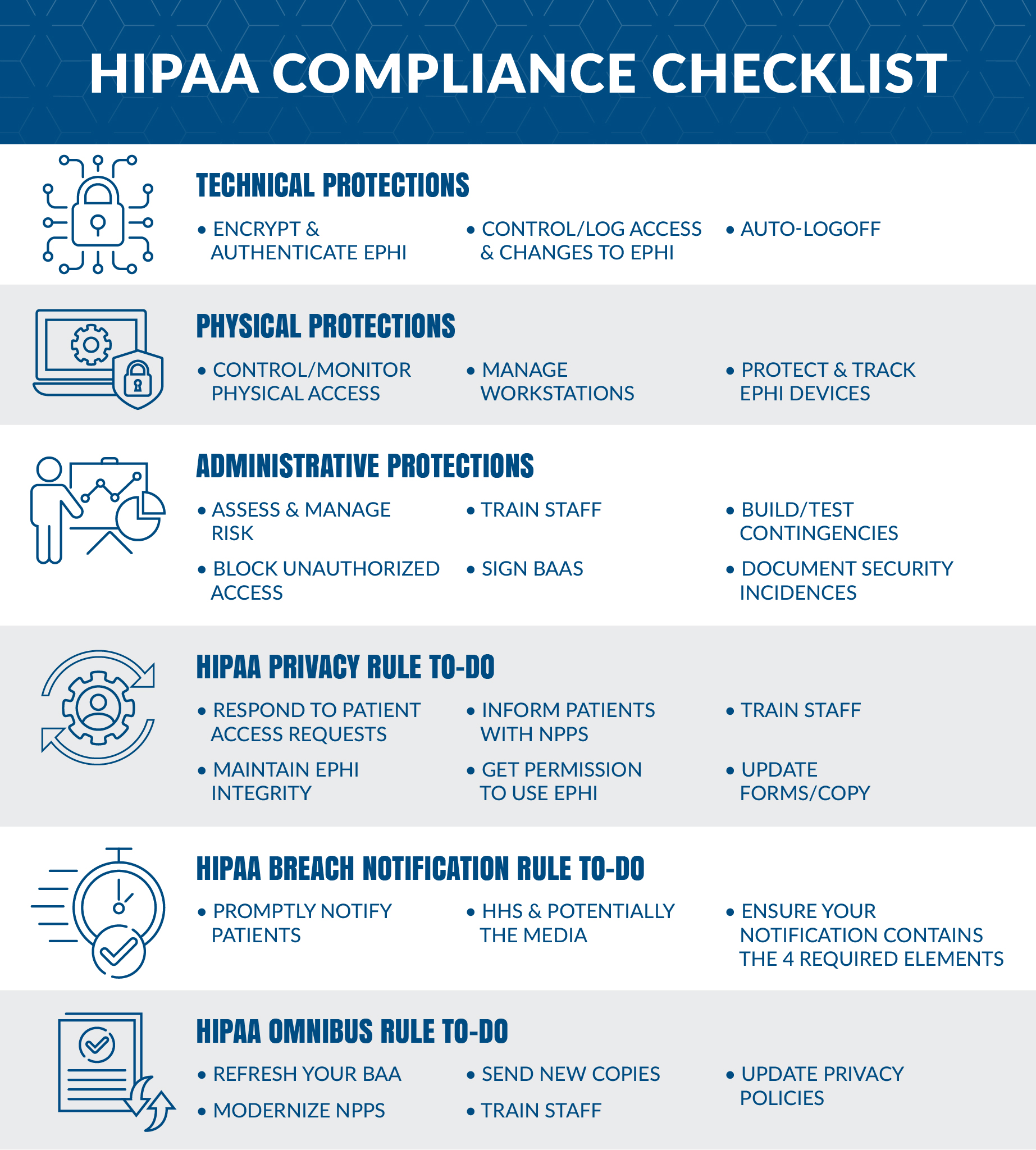
Hipaa Compliance Checklist What Is Hipaa Compliance
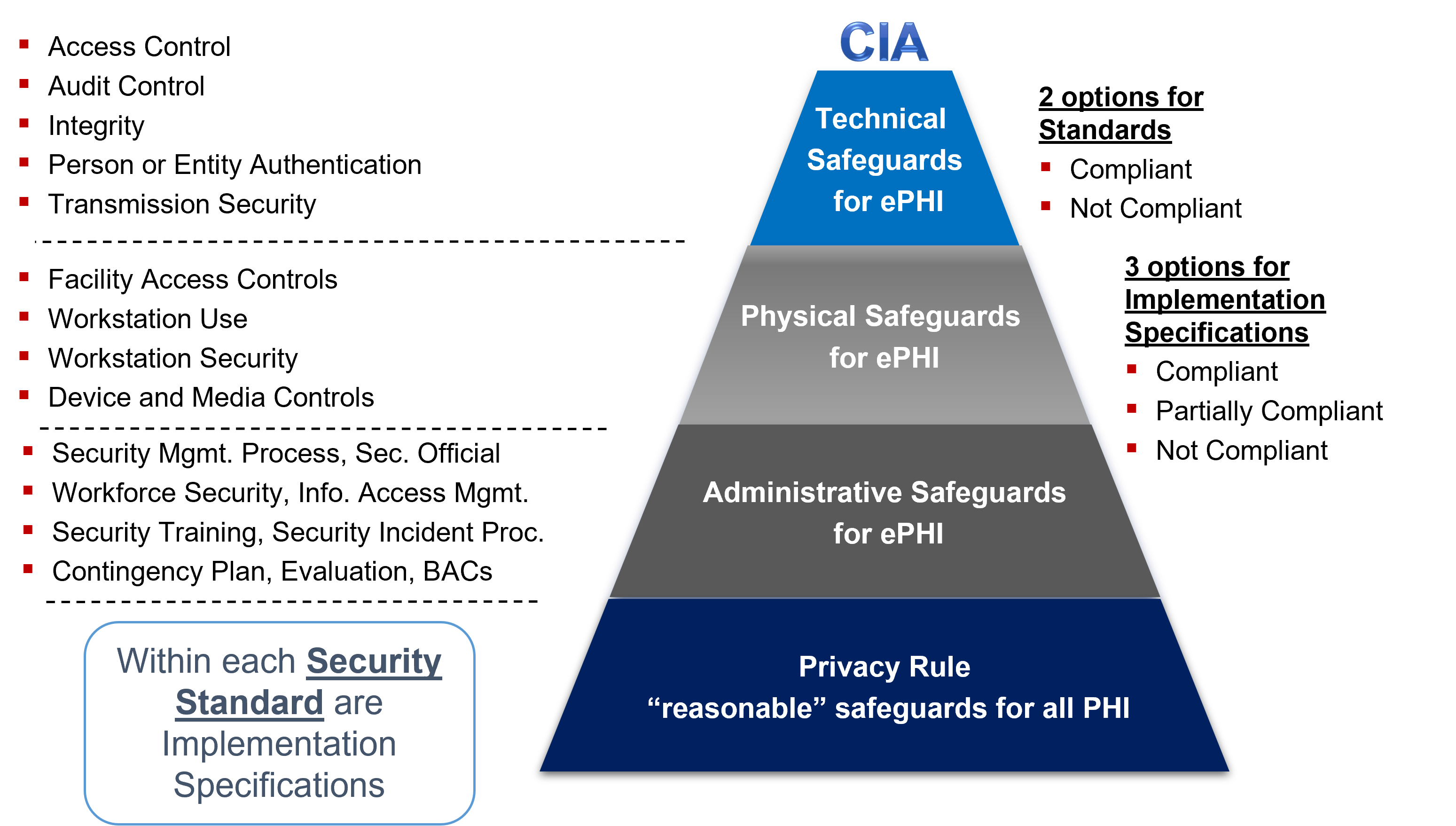
Hipaa Security Rule Hipaa Academy Beyond Hipaa Hitech Mu Ehr Health It Health Insurance Portability And Accountability Act
Comments
Post a Comment